The cores uses generic Intel altsyncram and Xilinx 7 series blockram macros and occupies ~720 registers and two ram blocks.
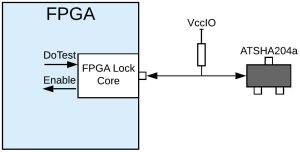
Only one pin on the FPGA is needed, and the only other component required is a pull-up resistor.
Within the FPGA, a clock, asynchronous reset and the trigger signal are required. The block’s output is the hash test result and device ID – the ID can be used for inventory control.
The company explained:
When triggered, the core reads the ATSHA204A’s unique ID, generates a random 256bit challenge and sends this to the [Microchip] IC.
The IC performs an NIST SHA256 hash on the challenge, a 256bit secret key that has been programmed into it, and its unique ID.
The result of this hash is then returned to the FPGA Lock core.
The core internally performs the same SHA256 hash with the challenge, secret key – which the core knows – and the device ID.
If the hash result returned from the ATSHA204A matches the values calculated by the core, then an ATSHA204A programmed with the correct secret key is present, and full FPGA functionality is enabled.
If not, then FPGA functionality is disabled.
Delaying the trigger for the hash test, it added, can be used to allow CEM hardware testing before the secret key has been programmed.
An accompanying core, called Key Writer, is used to programme the user’s custom secret key into the ATSHA204A, and then secure it against illicit access.
Both cores come in plain VHDL. Example Quartus and Vivado builds for Intel Cyclone 10 and Xilinx Artix 7 FPGAs are available.
Licensing in on a site basis, and can be used in any designs generated in that location.
The FPGA Lock product page can be found here
www.nialstewartdevelopments.co.uk/fpga_lock.htm
 Electronics Weekly Electronics Design & Components Tech News
Electronics Weekly Electronics Design & Components Tech News