Fill in a simple on-line form and, using publically-available data and some information trawled from live geo-location phone apps, it will tell you if the person is at home or not.
It doesn’t work for everyone, it depends how connected your potential victim is.
Take the Electronics Weekly UK Salary Survey 2014 »
A monstrous evil on the web? Some say it is, which is why there isn’t a link to it here, but it was created for good – to warn people that thieves are already using the same data – to demonstrate the consequences of putting too much of your life on the web.
Spool forward a few years. IPv6, wireless sensors, and cloud services are making life easy – the Internet of Things (IoT) is upon us. People can create ad-hoc home automation using mash-ups on their phones.
Going out for a while? Need some security? Simple: drag the Bluetooth speaker icon onto your phone screen, drop the doorbell icon on top of it, send a file called ‘dogs.mp3’ to the speaker, and, hey presto, every time someone pushes the doorbell, they hear a dog barking.
You have increased the security of your home, or so you think.
But what if someone has automated far more than the burglary website above, and has produced a readily-available phone app that can sift through IoT data to find the nearest house whose status suggests it is empty.
Through the internet this hypothetical app can see dogs.mp3 on the speaker, it can see the doorbell-speaker link, and it can see the smartFridge is set to ‘no auto-replenish’. It knows that you are on holiday.
Another app might allow a house to be scanned for Wi-Fi and Bluetooth activity. Drop a phone running the app into someone’s hedge. Retrieve it the next day, and see if anyone inside has interacted with anything.
It will be a thieves dream.
And it will never happen, says Haydn Povey, but only if IoT product developers design security in from the ground up. And Povey should know, as part of his job at ARM is as an evangelist for secure machine-to-machine communication.
“My job is to educate people, to make the internet-of-things secure on delivery,” Povey told Electronics Weekly. “The first internet fridge was hacked, and a lighting system has been hacked. Preventing this is just a set of good practices. There are good solutions already. It can all be done today with existing technology.”
| Internet of things? To bring some sanity to the hype, we are defining the Internet of Things as anything that uses internet protocol to communicate. Version 6 (IPv6) uses 128bit internet protocol (IP) addresses and allows an astronomical number of things (2128) to have their own address on the internet. Plus we add any sensor that communicates wirelessly to an edge-node on the internet. Wired sensors are excluded here because they can’t be snooped from outside a building. One of the reasons IP is being employed is to speed product development because: there is no need home-brew a proprietary protocol, the protocols stacks are already available, 32bit microcontrollers that can run the stacks are now cheap and consume little power, and smart devices like phones already speak the language. |
People will need good reasons to have confidence in the IoT:
Devices have to be secured against hacking, even where firmware up-dates are possible.
Communications must be encrypted all the way to the consuming application.
There must be some way to control privacy.
“I don’t want to scare people. We have to be realist for now and look at theoretical growing risk for the future,” said Povey. “If we plan for worst case, it will be too expensive.”
So, a wireless thermostat mustn’t transmit in such a way as to indicate a house is empty – each message it sends must be encrypted in a way that messages change even when the temperature stays the same – but its security key can be written on the back of the enclosure because if someone can read it, they have already broken in.
“Measure the temperature, encrypt, send it over the home network or internet, unpack it, and see the temperature at far end,” said Povey. “We are strongly behind using public key infrastructure [PKI], with a set of keys on the device. It will all be 128bit encryption.”
PKI secures a link using clever maths and a private key at one end of a link and a corresponding public key at the other.
The set of unique private keys, one for normal communications and one for firmware updates, for example, will be burned into the product during manufacture.
Pairing must be easy. Few people are going to type a 128bit hex string off the back of the back of a new thermostat into the central heating controller, but an NFC touch on the controller is easy, as are a bunch of other options – for example a short code that will tell the central heating controller to go to a central website and collect the correct 128bit keys to speak to the thermostat.
“As an industry, we need to get a standard way of using identification [ID] and authentication: standard infrastructure and standard mechanism,” said Povey.
Privacy is hardly an issue for a thermostat, but it is for a smart running machine in a public gym. “At the gym, I might want data to go to my cloud service and to my phone when I am on the running machine, and I may want to share with my coach, and friends through a fitness app. I will accredit with the machine using NFC or tapping in a number,” said Povey. At the same time “the machine will be logging data for the maintenance company, and it may be leased, so the owner might want data for depreciation.” There are many users of data here, and the data has to be anonymous to some of the users.
To manage webs of privacy, trust is important. In this case, the running machine is the trusted item. By design, it must include mechanisms to gather and disseminate data only to those accredited to see it, and only in the form they are accredited to see.
Accreditation in each case must be via a unigue identifier through a mechanism appropriate to the data type – a running machine is not a bank account or the door to a nuclear power station. Security is fundamental to trust. The running machine is a trusted item, so it must be hack-proof.
How do you manage all this accreditation and security? “Public key encryption,” said Povey.
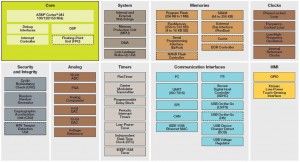
To implement it, microcontrollers are available with built-in encryption engines. These are not always necessary. “If it is a small amount of data occasionally, a thermometer for example, you can do it all in software. It depends on the amount and type of data. There is also the software-plus-hardware-accelerator option,” said Povey. “It also depends on the encryption standard: DES, triple DES, AES. Probably for IoT, elliptic curve crypto [ECC] is a bit more power efficient.”
 Electronics Weekly Electronics Design & Components Tech News
Electronics Weekly Electronics Design & Components Tech News