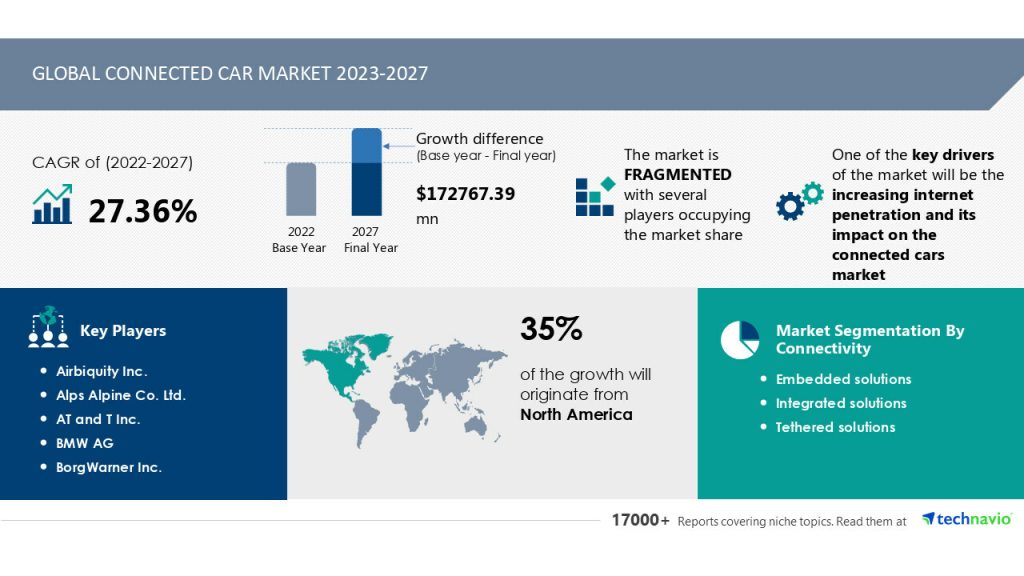
Figure 1 – Technavio has announced its latest market research report titled Global Connected Car Market 2023-2027
As more vehicles become more connected and thus vulnerable to malicious cyber attacks, the importance of managing cyber risk grows. Cyber risk management is guided by a number of standards and regulations and involves a layered defense in depth approach that touches on safety, security, and reliability. The ISO 26262 standard for functional safety in the automotive industry covers IC defects that are either present at manufacture or manifest during the lifecycle of the vehicle. The ISO 21448 standard is more focused on operation correctness as it looks at the function of the device within the system to ensure that it operates as intended. The ISO 21434 standard guides cybersecurity risk management throughout the silicon lifecycle. What is a cybersecurity lifecycle? It includes the product concept, development, production, operation, maintenance and end-of-life for electrical and electronic systems.
Vehicle makers and OEMs then, will be busy finding and securing weaknesses that hackers can use to endanger the safety of the car, steal user information, or interfere with automotive data.
Automotive cyber attack examples
The Secure-CAV Consortium offers some concrete examples of hacks. One is a mobile network attack in which an attacker tries to infect the Telematic Control Unit with tampered firmware. This uses a “man in the middle” type of attack to make an over-the-air firmware update. If successful, hackers could intercept telematics traffic using GSM and can spoof the SMS commands, sending direct commands to the device. The consequences range from the hackers gaining access to the infotainment unit, to denial-of-service attach against emergency services, to controlling the engine, transmission or brakes.
Effective vehicle cybersecurity
While the functional safety risk landscape is essentially static for a given function, the security threat landscape is very dynamic— the type and complexity of cyber security attacks change throughout the lifecycle of the vehicle. Considering that by the time most vehicles hit the market, the electronics technology used is already several years old, security features built into the system today could be out of date even before the vehicle goes into production. This is the compelling reason to develop security technology that is also extremely dynamic and adaptable to whatever future threats present their selves. A challenge to this goal lies in how to know what solutions will be dynamic and adaptable.
The Secure-CAV platform
The Secure-CAV Consortium has developed a flexible and functional architecture for real environment trials to train, test, validate and demonstrate automotive cybersecurity solutions. The goal is to faithfully and accurately reproduce the behavior of a real vehicle while also being reconfigurable, portable, safe, and inexpensive to construct. The testbed gives the cybersecurity researchers and engineers comprehensive security evaluation of in-vehicular network components providing:
- Integration of Siemens EDA IP in an FPGA implementation for ECU behavior monitoring
- Support for multi-component architecture and a range of on-board communication protocols (including CAN and Automotive Ethernet)
- A ‘plug-and-play’ facility for client ECUs (which may be telematics units, sensors, infotainment systems, in-cabin connectivity, and body modules)
- A traffic scenario simulator to generate sensor data and connectivity supporting threat use cases being demonstrated
- Configurability for repeatable test scripts, and an interface for packet injection and tracing, to support attack vectors
- A data repository for data captured from emulated sensors, vehicle simulator, CAN/Automotive Ethernet payload, FPGA, and attached ECUs for visualization, test calibration, and machine learning. The repository could be in-cloud for remote analysis or on local storage.
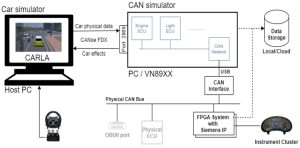
The Secure-CAV automotive cybersecurity testbed includes a car simulator, an on-board network simulator, a field-programmable gate array (FPGA) system, a physical network, data storage, and a real car’s instrument cluster (Figure 2). Most of the vehicle architecture and its CAN bus network is realized within a virtual environment using Vector CANoe network simulator. The data collected can be analyzed and used to update the embedded monitors on the FPGA.
Figure 2. The Secure-CAV demonstrator architecture.
The IP and anomaly detection software in the Secure-CAV demonstration vehicle monitors protocols and transactions at the lowest level in hardware. This is backed by unsupervised machine learning algorithms and statistical analysis, with expert input from the University of Southampton. This was integrated into FPGA technology and linked to two vehicle demonstrators developed by teams at Coventry University and cybersecurity specialists Copper Horse (Figure 3). A range of selected real-world threats has been exercised, including purchasing and analyzing hacking equipment for existing vehicles.
Figure 3. The Secure-CAV platform faithfully and accurately reproduces the behavior of a real vehicle.
The embedded IP (Tessent Embedded Analytics) used for on-chip data collection forms the underlying foundation of the Secure-CAV system. The embedded IP can also be designed into automotive devices themselves, to monitor the device through its lifecycle, providing the underpinning layers of a defense in depth strategy. Not only do these embedded IP detect potential threats through structural and function monitoring, but they can take action to block them. Here’s a partial list of the security features addressed by Siemens’ Tessent Embedded Analytics:
- Secure boot – Hardware monitoring technology can be used to check a prescribed boot sequence has been executed as expected. This ensures that both the hardware and software are as intended.
- Attestation – Similar to secure boot, functional monitoring can be used to generate dynamic signatures that represent either a hard or soft configuration of a specific IP or IC in a system. This confirms again both the accuracy of the expected hardware and its configuration. This approach can be used to provide either a single identity token or a system wide collection of tokens.
- Secure access – As with all systems, it is critical that communication channels in and out of the device are secure and, in many cases, configurable based on different levels over required access.
- Asset protection – Active functional monitoring can be a critical part of any defense in depth strategy against the dynamic cyber-threat landscape. Based on a detailed threat analysis, selection and placement of functional monitors within the device provide extremely low latency threat detection and mitigation.
- Device lifecycle management – Auto-makers need to be able to monitor the health of the IoT devices throughout their active life cycles, from manufacture through to decommissioning. Functional monitoring and sensors play a significant part in monitoring device health over their life cycle.
The data collected from automotive devices in the field are part of a larger automotive lifecycle scheme that includes fleet management, embedded software, a cloud platform like Siemens’ MindSphere, and product lifecycle management.
Figure 1. Expect strong growth in the connected car market.
Figure 2. The Secure-CAV demonstrator architecture.
Figure 3. The Secure-CAV platform faithfully and accurately reproduces the behavior of a real vehicle.

Author, Lee Harrison is Automotive IC Test Solutions Manager within the Siemens Digital Industries Software Tessent group and has responsibility for the company’s automotive test solutions. His previous position was manager of DFT consulting services at Mentor Graphics, where he managed a worldwide team of consultants delivering DFT and test solutions in many different product domains. He has also held senior engineer positions at 3COM and BAE Systems. He received his BEng in Microelectronics and Brunel University, London, UK.
 Electronics Weekly Electronics Design & Components Tech News
Electronics Weekly Electronics Design & Components Tech News