Even the programmer-to-MCU connection is secured against ‘sniffing’, because captured signals are one-time encrypted.
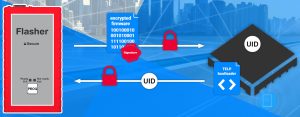
The scheme is implemented by the company’s Flasher Secure programmer hardware, combined with software dubbed ‘Telp’ for ‘target encrypted link package’.
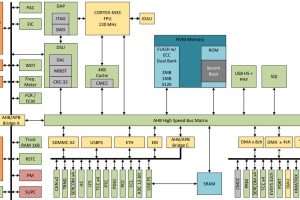
It works like this:
The flasher (programmer) at the third party or remote site, interrogates the MCU, requesting its unique identification number – minimum MCU requirements are a unique ID, 8kbyte of flash and 8kbyte of RAM.
Via an encrypted link, this ID is sent back to a secure server by the flasher, where a digital signature is generated and sent back to the programmer if the ID is authorised. Firmware is transferred during this step if it is not already at the flasher.
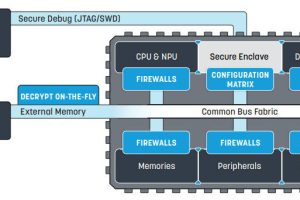
With this authorisation, the flasher installs a secure boot-loader onto the microcontroller, which includes an encrypted communication protocol and “a proprietary method”, said Segger, that enables TELP to switch off the debug interface.
Now the flasher can communicate with the MCU via a mutually-encrypted channel, and it is through this that the encrypted firmware download is completed, after which the MCU decrypts and installs its own firmware, and deletes the boot loader.
“Every device is programmed using mutually-agreed unique session keys for the encrypted link, and without those keys the captured trace is useless. Together, they ensure end-to-end IP security and protection against attacks of any kind,” claimed Segger. “IP owners and contract manufacturers alike benefit from having the owners in complete control of the programming process. The contract manufacturer never has access to the clear-text of a firmware image and both gain the peace of mind of ensuring the protection of IP from copying, cloning, and unauthorized production.”
 Electronics Weekly Electronics Design & Components Tech News
Electronics Weekly Electronics Design & Components Tech News